Cyberattacks continue to wreak havoc on businesses and governments, making cyber security an issue of increasing interest to company managers and governments. One in five companies receive cyber threats and attacks. The most common threats are related to data, supply chain or people, with email being the main gateway for cybercriminals.
According to a study by Hornetsecurity, associated economic losses amounted to about 945 billion dollars worldwide in 2020, double the amount registered in 2018. Cyberattacks have dramatic consequences, and not only financial. They also affect opportunity costs, damaging the brand and resulting in a great loss of systems and productivity.
What kind of cyberattacks are the most frequent?
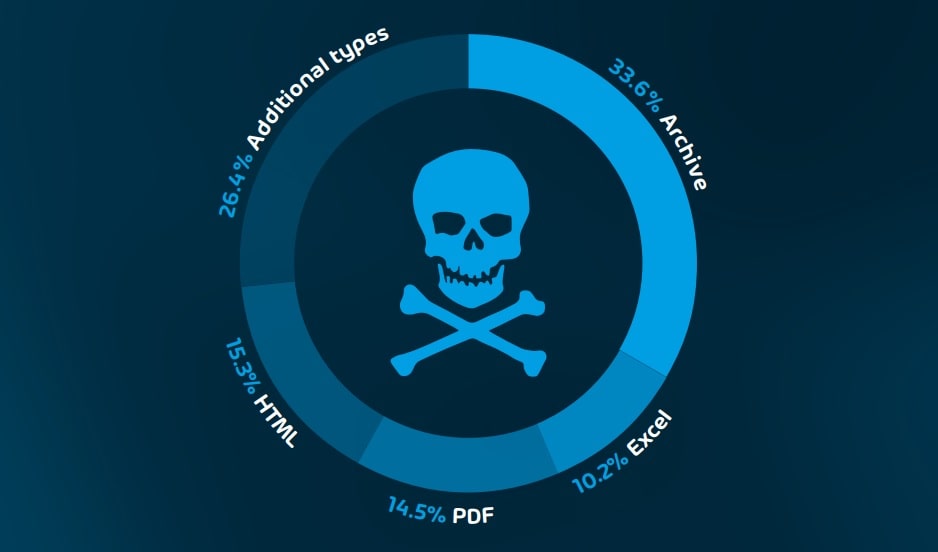
Private information and sensitive data are the perfect target for cybercriminals. Email is the main channel of access, generally through the use of malicious attachments. The most commonly used attachment types in malicious emails are compressed (such as .zip or .rar), HTML, PDF, and Excel files.
In 2021, the sectors most affected by cyberattacks were those involving research and development, the manufacturing sector and public transport companies, including railways, buses, taxis and airlines. Other affected sectors are related to education, entertainment, hotels, and the agricultural and health sectors.
Most commonly used cyber threat methods
Brand spoofing, phishing, and ransomware remain among the most commonly employed attack tactics. The following section will discuss some of these techniques:
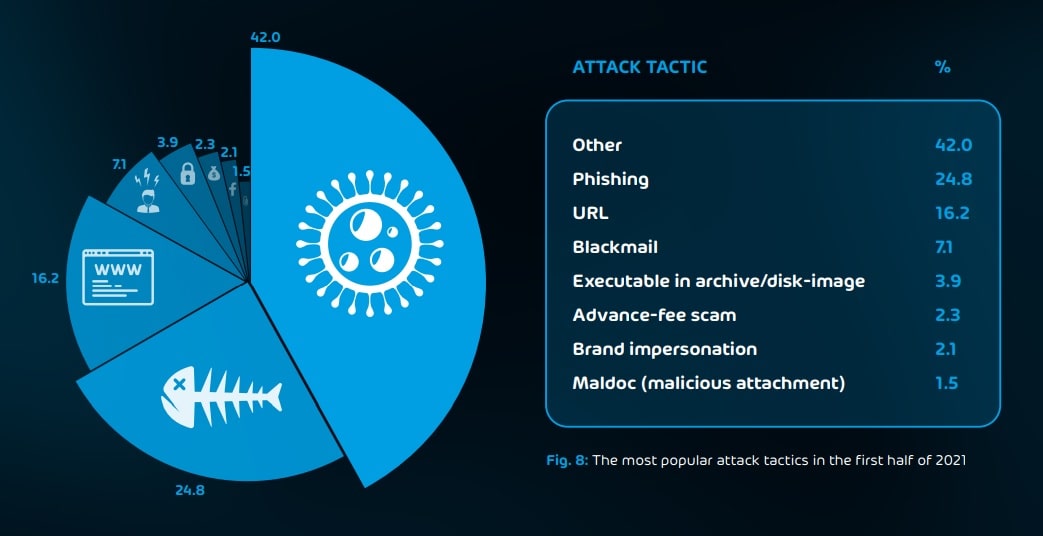
- Phishing emails. Hackers use this method to try to gain access to sensitive data. They search for information ranging from access data to passwords and debit or credit card information. They often make use of extortion, blackmail and sextortion. In the latter technique, the person receives an email informing them of the existence of a video showing them visiting pornographic websites. The victim is told they need to pay a ransom to prevent the video from being made public.
- Brand impersonation. These cyberattacks imitate well-known brands through small variations in their logos in order to gain access to usernames and passwords, bank card details, or to get the recipient to accept a malicious link that downloads malware onto their system without realising it.
- Ransomware. This technique is based on the publication of information that is confidential or sensitive for the victim on data leak websites. Here, cyber attackers make a copy of the files on the server and threaten the victim with publishing their data if they do not accept their demands. Their targets are usually companies, but also public figures and governments.
New types of cyberattacks on companies
The digital world continues to grow, and with it, cybercrime. Hackers are becoming more professional, establishing networks to help them carry out large-scale attacks. In addition, cyber attackers are known to employ greater effort in carrying out reconnaissance tasks to discover security gaps. In addition, they use new digital tools to carry out their attacks.
More importantly, they are taking advantage of new vectors to launch new attacks on Linux-based systems, which were previously unaffected by cyber threats. An example of this is Vermilion Strike, which can launch an attack remotely without being detected.
“Living off the land” attacks are another new type of attack that are based on the use of malicious files that do not need to be developed from scratch. These take advantage of existing computer system points of access. This is how they access trusted programs using malicious code. This malware is able to bypass traditional security systems and then infiltrate them and steal sensitive information while avoiding detection.
How can you protect yourself from cyber threats?
Cyber threats are on the rise and cybercriminals are expected to increase their activity in the future. For this reason, it is important to develop effective and advanced cyber security strategies to prevent any damage.
Centralising cyber security will help ensure implementation of security policies, and guarantee that systems are updated and configured in a timely manner; threats and suspicious events will be detected so that they can be stopped, preventing cybercriminals from achieving their objective.
In conclusion, people working for companies or public entities should ideally become familiar with the potential for cyberattacks, especially now, with teleworking on the rise. Only then can the appropriate measures and precautions be taken.
Tech2Business is a company with solid digital expertise. We are convinced that the fight against cybercriminals is one fought with daily up-to-date actions in order to combat the ever-changing world of cyberattacks and associated methods. Accordingly, we offer various custom cyber security solutions for different companies and public and private entities. As digital product wholesalers, we can help you. Want to learn more without any obligation to purchase? Don’t delay!

